The #1 Reason Hackers Keep Winning — And It's Not What You Think
- 3 days ago
- 3 min read
💥 Introduction: It’s Not About Code Anymore
You’ve got antivirus. You use strong passwords. You enable 2FA. You verify your social profiles. You lock your phone.
But there’s one place you still trust without thinking:
📩 Your email inbox.
And that’s exactly where the next breach begins.
Because hackers don’t need to break in. They just need to be believed.
Most people think cybercrime is about elite hackers and complex malware. In reality, it’s usually just a well-written email that looks like it came from someone you trust.
⚠️ The Real Reason Cybercrime Works in 2025: Trust
Email is still the #1 attack vector because we blindly trust:
Sender names
Brand logos
Familiar layouts
Subdomains that “look close enough”
And it’s that false sense of confidence that hackers rely on.
It’s not a technical breach. It’s a psychological one.
💬 Real Example: How One Fake Email Cost $48,000
In April 2025, a finance manager at a growing tech company received an urgent message:
From: ceo@company-finance.com
Subject: Immediate wire transfer request “Please wire $48,000 to the new vendor account today. Confirm once done.”
The email looked familiar. The tone matched previous conversations. But it wasn’t the CEO. It wasn’t even the right domain.
No DMARC policy.
No S/MIME signature.
No DNSSEC validation.
✅ It passed spam filters
✅ It looked real
❌ It wasn’t real
Result? The company lost $48,000 — and never got it back.
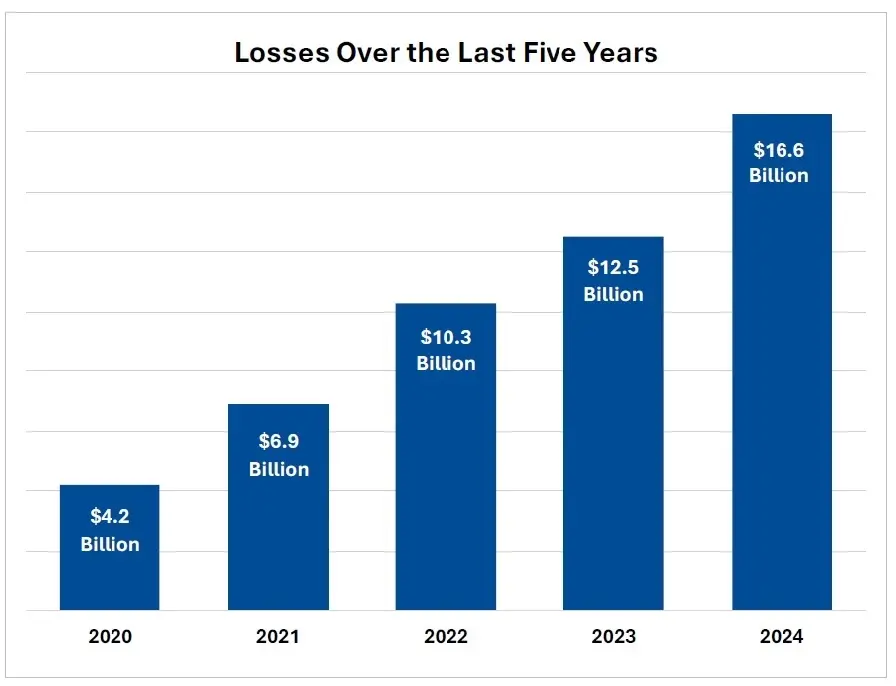
Cybercrime by the Numbers (2025 So Far)
Let’s be clear — email isn’t just “a” risk. It’s the risk.
According to FBI IC3, ENISA & DBIR reports:
💥 93% of cyberattacks start with email
💰 $6.9B in BEC (Business Email Compromise) losses in just 6 months
🧪 72% of phishing emails use brand impersonation
🔐 Only 8% of domains enforce strong DMARC with subdomain protection
⚠️ Less than 15% of domains implement DNSSEC
📩 Only 0.7% of emails are signed with verified identity (S/MIME)
🔎 The Hidden Backdoor: Subdomain Spoofing
You check for @paypal.com or @tesla.com. But hackers use:
@secure-update.paypal-support.com
@billing.dhl-contact.net
@alerts.tesla-finance.org
And unless DMARC with sp=reject is in place, those subdomains aren’t protected.
The brand looks real. The email feels urgent. And your trust does the rest.
🔐 The Technical Problem Behind the Human One
Even tech-savvy users are vulnerable when the domain infrastructure itself is broken.
Here's what's missing:
Layer | Problem | Impact |
DMARC | Missing sp=reject for subdomains | Subdomain spoofing possible |
DNSSEC | Not implemented or broken | DNS record tampering allowed |
S/MIME or PGP | Not adopted by most users | Sender identity can’t be proven |
Real Solutions That Work
You don’t need bleeding-edge tools. You just need to enforce what already exists.
1. ✅ DMARC + sp=reject
Ensure both root domain and subdomains are protected.
2. ✅ DNSSEC
Validate that no one has modified your DNS records mid-path.
3. ✅ S/MIME or PGP (Digital Signature)
Sign your email with a cryptographic ID. Let inboxes and recipients see: “Yes, this really came from me.”
🧠 Final Thought
Cybercrime isn’t thriving because tech has failed. It’s thriving because people still trust what looks familiar.
And email?It’s still treated as a trusted channel — even when it’s the most impersonated surface in the digital world.
Until we make verified identity and domain-level trust the default,
Hackers won’t need to hack. They’ll just send… and wait for you to believe.


Kommentare